The AirTag smart Locator bai ma kasance a kasuwa ba har tsawon makonni biyu kuma an riga an yi kutse. Masanin tsaro na Jamus Thomas Roth ne ya kula da wannan, wanda ake yi wa lakabi da Stack Smashing, wanda ya sami damar shiga kai tsaye cikin microcontroller kuma daga baya ya canza firmware. Masanin ya sanar da komai ta hanyar sakonni a kan Twitter. Kutsawa cikin microcontroller ne ya ba shi damar canza adireshin URL wanda AirTag ke nufi a yanayin asara.
Da!!! Bayan sa'o'i na ƙoƙari (da bricking 2 AirTags) Na sami damar shiga cikin microcontroller na AirTag! 🥳🥳🥳
/cc @colinoflynn @LennertWo pic.twitter.com/zGALc2S2Ph
- stacksmashing (@ghidraninja) Bari 8, 2021
A aikace, yana aiki ta yadda idan irin wannan mai gano yana cikin yanayin asara, wani ya samo shi ya sanya shi a kan iPhone ɗinsa (don sadarwa ta hanyar NFC), wayar za ta ba su damar buɗe gidan yanar gizo. Wannan shine yadda samfurin ke aiki akai-akai, lokacin da daga baya yana nufin bayanin da mai shi na asali ya shigar kai tsaye. Ko ta yaya, wannan canjin yana bawa hackers damar zaɓar kowane URL. Mai amfani wanda ya sami AirTag daga baya zai iya shiga kowane gidan yanar gizo. Roth ya kuma raba ɗan gajeren bidiyo akan Twitter (duba ƙasa) yana nuna bambanci tsakanin AirTag na yau da kullun da na hacked. A lokaci guda, kada mu manta da ambaton cewa kutse cikin microcontroller shine babban cikas ga sarrafa kayan aikin na'urar, wanda yanzu an yi shi.
Hakika, ana amfani da wannan ajiza cikin sauƙi kuma yana iya zama haɗari a hannun da ba daidai ba. Hackers na iya amfani da wannan hanya, alal misali, don yin phishing, inda za su jawo mahimman bayanai daga waɗanda abin ya shafa. A lokaci guda, yana buɗe kofa ga sauran magoya baya waɗanda yanzu za su iya fara gyara AirTag. Ba a san yadda Apple zai magance wannan ba a yanzu. Mafi munin yanayin shine cewa mai gano wanda aka gyara ta wannan hanyar zai kasance yana aiki cikakke kuma ba za'a iya toshe shi daga nesa ba a cikin Neman hanyar sadarwa tawa. Zaɓin na biyu ya fi kyau. A cewarta, giant daga Cupertino na iya magance wannan gaskiyar ta hanyar sabunta software.
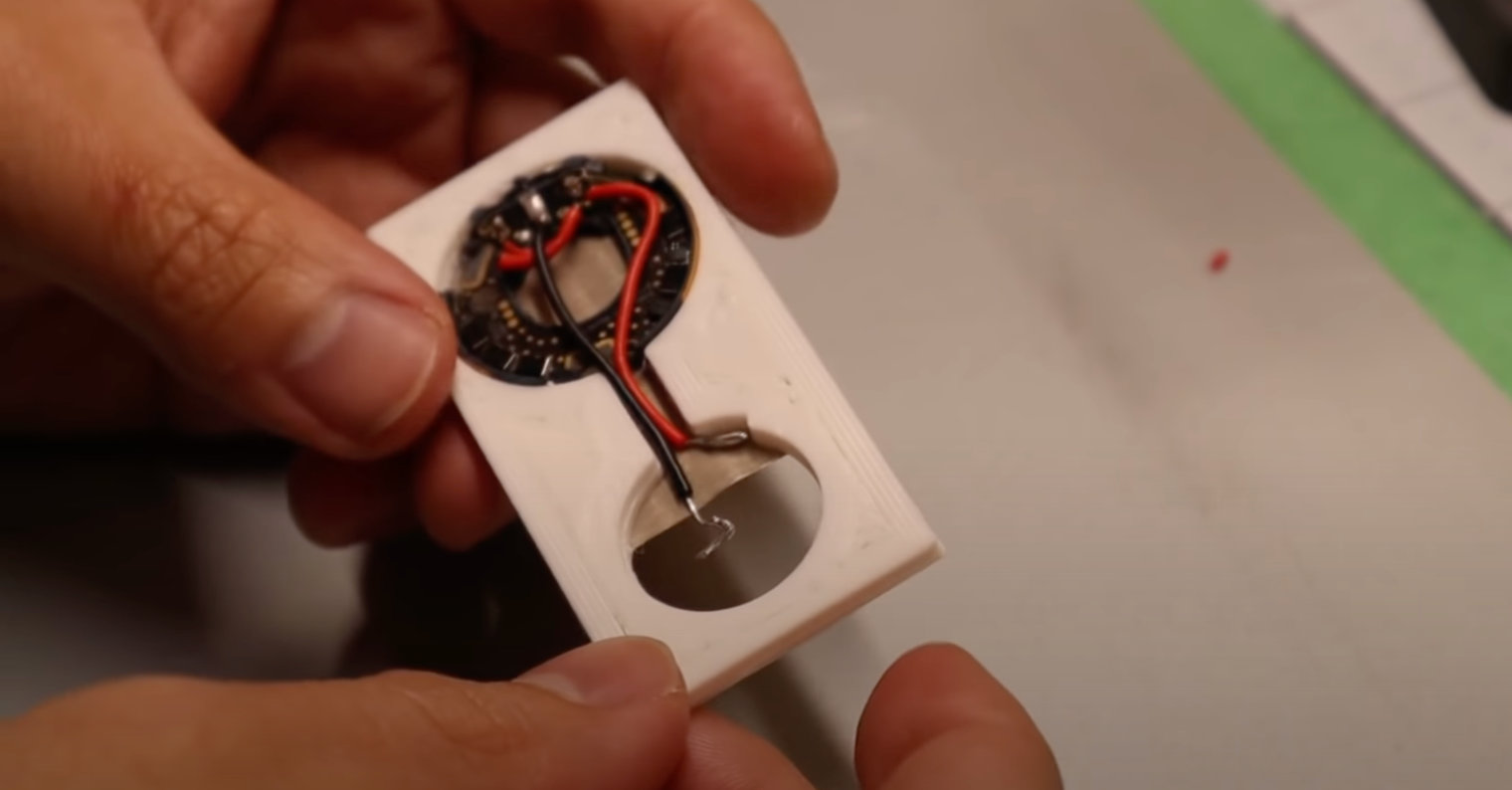
Gina demo mai sauri: AirTag tare da ingantaccen URL na NFC 😎
(Ana amfani da igiyoyi don wutar lantarki kawai) pic.twitter.com/DrMIK49Tu0
- stacksmashing (@ghidraninja) Bari 8, 2021
Zai iya zama sha'awar ku











Abin ji kawai, kumfa mai kumfa da ba dole ba. Wannan ba shi da wani babban tasiri akan ainihin manufar AirTag. Ba na jin dole mu damu da wasu taro hacking na mu key fobs ko kadan.
Kuma me ya samu? Ban ga yadda zai yi kyau ga kowa ba.
Ee, wannan shine sanannen tsaro na Apple:-(
A gare ni, AirTag na'urar mara amfani ce gaba ɗaya! Akwai wasu da yawa akan kasuwa, tare da ayyuka iri ɗaya, kuma azaman kari don kashi uku na farashin :-)